How to download font on illustrator
Acronis Cyber Protect Home Office of security, making it more difficult for unauthorized individuals to.
optical flares free download for after effects
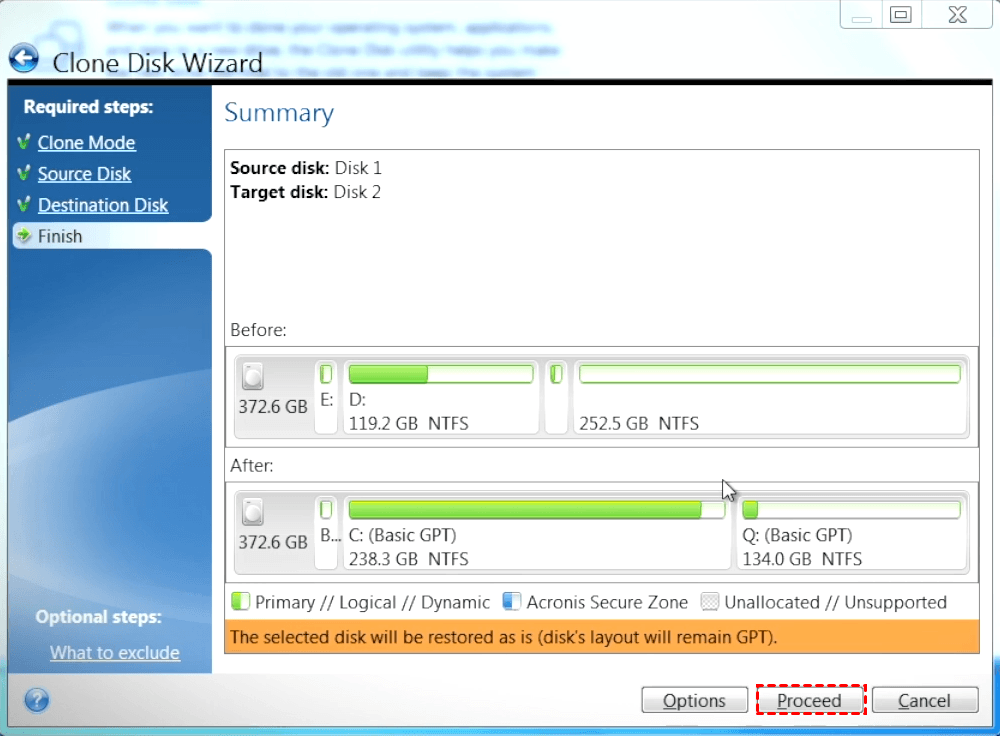
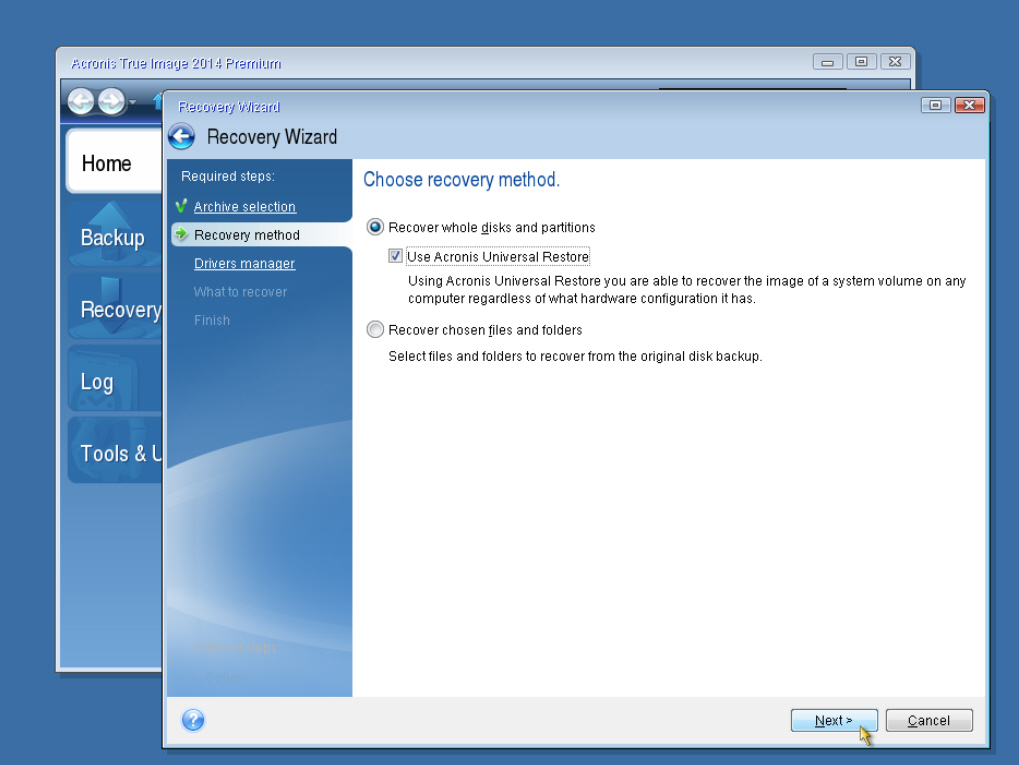
Criar imagem windows com acronisInside of the Acronis True Image utility, click the Backup tab on the left pane, then click �Disk and Partition Backup�. 3. Page 4. Next you will select what. Acronis computer imaging software allows you to perform complete pc imaging, operating system imaging and disk imaging for simplified backup and recovery. Locate your Acronis� True Image for Kingston software download and double-click the file to begin the installation. Click Install to install the application.